Instantly.ai Review for Founders
•
Founders and small outbound teams want a cold email tool that actually works. This Instantly review focuses on what matters most: deliverability, inbox rotation, automation, AI features, pricing, and real-world performance. It pulls from hands-on tests across multiple domains and sending accounts, plus feedback from G2 and Reddit. Instantly.ai stands out because it connects…

Apollo.io Review – What It Does, Who It’s For, and How It Performs
•
Apollo.io is a straightforward all-in-one platform that combines B2B contact and company data with outreach tools. It brings email sequences, a dialer, tasks, and light CRM features into one simple interface. Early-stage sales development reps get value from fast list building and quick outbound without bouncing between apps. Pre-seed and seed founders avoid the…

Proton VPN Review – Can You Really Browse Safely?
•
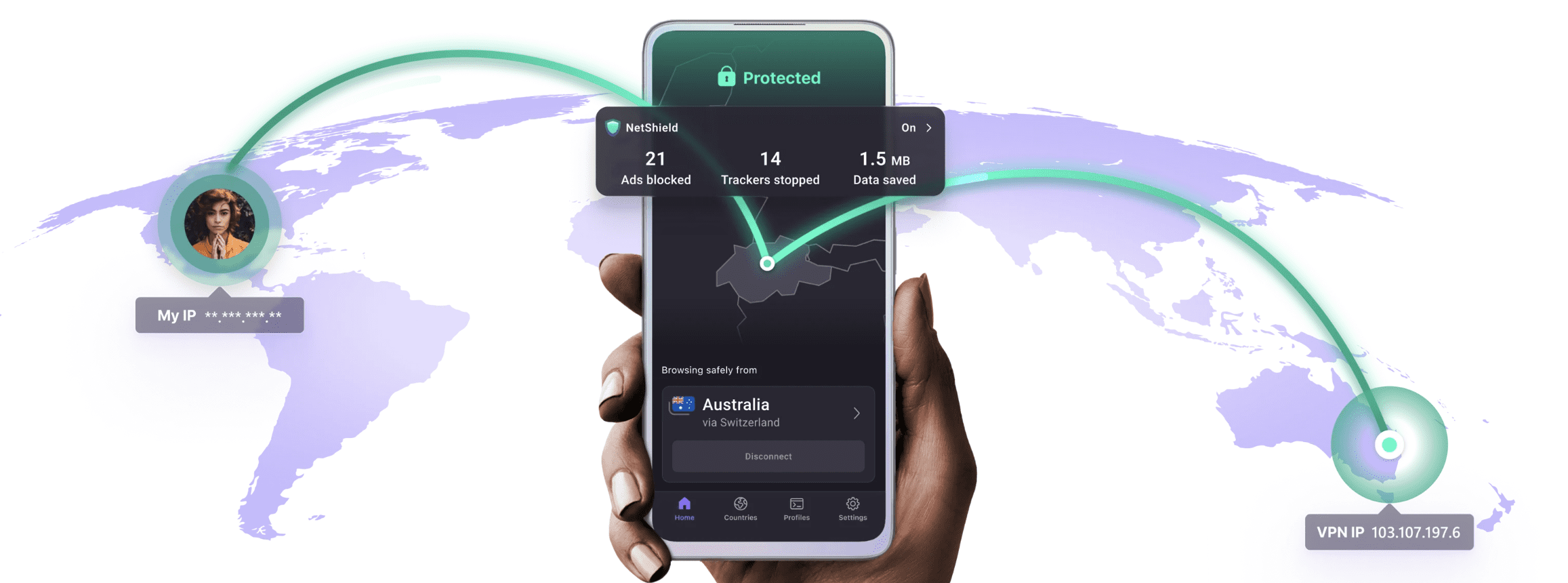
Proton VPN enters as a privacy-first service based in Switzerland, a country with strict data protection laws that carry weight. The company focuses on safeguarding user data and keeps the message plain. The brand builds on clear privacy principles and practical usability. This review looks at what Proton VPN offers for people who want…

Proton Mail Review – Is it really secure?
•
Email is still the main doorway attackers try first when targeting regular people and small teams. Phishing often starts there, tricking users into giving up passwords or clicking bad links more than anywhere else online. Locking down an inbox isn’t about spam alone. It’s about protecting private conversations and sensitive data from snoops. Proton…

Proton Calendar Review – Why a Secure Calendar Matters
•
A small startup lost track of key sales meetings, and the cause wasn’t a hacker smashing firewalls. A shared calendar invite spread too far, exposing links to private video calls and wrecking their pipeline. Calendar invites now double as a quiet attack path. Phishing links hide inside normal-looking events and slip into busy schedules.…